Fake Zoom Link Targets Crypto Users, Leads to Multi-Million Dollar Theft: SlowMist Warns

A detailed report by blockchain security firm SlowMist reveals that a sophisticated phishing attack disguised as a fake Zoom meeting link has stolen crypto assets worth millions.
The scam, first identified on November 14, 2024, targets users by distributing malicious software through links that mimic the legitimate Zoom interface.
After digging deep, this phishing campaign has been linked to Russian-speaking hackers. The stolen funds were tracked to various crypto platforms, including Binance, Gate.io, and Bybit.
⚠️Beware of phishing attacks disguised as Zoom meeting links!🎣 Hackers collect user data and decrypt it to steal sensitive info like mnemonic phrases and private keys. These attacks often combine social engineering and trojan techniques. Read our full analysis⬇️… pic.twitter.com/kDExVZNUbv
— SlowMist (@SlowMist_Team) December 27, 2024
The Phishing Scheme: How Hackers Use Fake Zoom to Steal Crypto
SlowMist’s investigation revealed that the attackers used the domain “app[.]us4zoom[.]us” to impersonate Zoom’s official web address.
The phishing site closely mirrored the legitimate Zoom meeting interface, tricking users into clicking the “Launch Meeting” button.
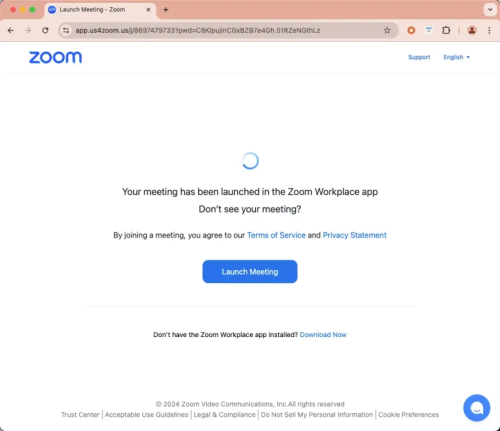
Source: SlowMist
However, instead of launching a meeting, the site downloaded a malicious package named “ZoomApp_v.3.14.dmg.”
Once executed, this package prompted users to enter their system password, granting the malware elevated permissions.
Upon further analysis, SlowMist uncovered a hidden executable file named “.ZoomApp,” which was embedded within the installation package.
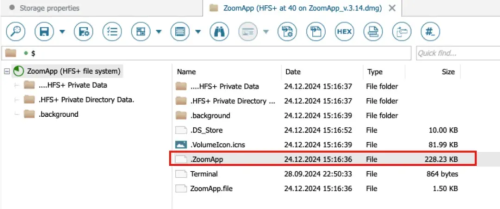
Source: SlowMist
This file acted as a Trojan, collecting sensitive user data, including system information, browser cookies, cryptocurrency wallet data, and KeyChain passwords.
The harvested information was then transmitted to a server controlled by the hackers, and its IP address, 141.98.9.20, was traced to the Netherlands.
Threat intelligence services flagged this IP as malicious.
The malware employed osascript scripts to bypass macOS security measures, allowing the attackers to steal wallet mnemonic phrases and private keys.
This enabled unauthorized access to victims’ crypto assets.
Furthermore, the attackers bypassed traditional security defenses by using social engineering tactics and exploiting trusted software.
Tracing the Stolen Funds: Hacker’s Trail Discovered
SlowMist utilized its on-chain tracking tool, MistTrack, to trace the movement of stolen assets.
The investigation identified a hacker address, 0x9fd15727f43ebffd0af6fecf6e01a810348ee6ac, profiting over $1 million.
Stolen assets included USD0++ and MORPHO tokens, which were subsequently swapped for 296 ETH.
The hacker’s address received small Ethereum transfers from 0xb01caea8c6c47bbf4f4b4c5080ca642043359c2e, an address suspected of providing transaction fees for phishing operations.
This address distributed small amounts of ETH to approximately 8,800 other addresses, suggesting it might be a transaction fee platform.
Further analysis revealed that part of the stolen funds was funneled to centralized exchanges, including ChangeNOW and MEXC, while 296.45 ETH was transferred to a new address, 0xdfe7c22a382600dcffdde2c51aaa73d788ebae95.
This address engaged in multiple transactions across different blockchains, with a current balance of 32.81 ETH.
The remaining funds were dispersed across platforms such as Bybit, Cryptomus.com, and Swapspace.
Notably, some of these transfers involved addresses flagged by MistTrack as linked to known phishing entities “Angel Drainer” and “Theft.”
As a result, Slowmist advises users to exercise caution and verify meeting links before clicking.
Key recommendations include:
- Avoid downloading software from unverified sources.
- Regularly update antivirus and anti-malware software.
- Refrain from entering system passwords for unknown applications.
- Monitor wallet activity and enable two-factor authentication (2FA) wherever possible.
Notably, a similar coordinated attack was reported earlier this month. The report indicated that Web3 workers are targeted by a sophisticated phishing campaign using fake meeting apps to steal sensitive information and crypto assets.
🚨Attention Web3 workers! According to a report from @CadoSecurity, a new scam is targeting Web3 workers with fake meeting apps designed to steal your info and crypto!#Web3Scam #CyberSecurityhttps://t.co/4Qlkq6XFru
— Cryptonews.com (@cryptonews) December 9, 2024
Attackers leverage AI to create realistic websites, blogs, and social media profiles for fictitious companies like Meeten and Meetio to appear credible.
Victims are lured into downloading malware-infected applications disguised as professional tools or business opportunities.
The malware, known as the Realst info-stealer, affects macOS and Windows devices and extracts credentials, financial data, and crypto wallet information.
Source: cryptonews.com