

A crypto wallet holds the private keys that control your digital assets on the blockchain. Most commonly, these wallets are applications, such as browser extensions or mobile apps. However, hardware wallets offer a more secure alternative as well, although at a cost. In this guide, we’ll review the most important things to consider and how to choose a crypto wallet that meets your needs.
Crypto exchanges provide custodial wallets to store your cryptocurrency after you buy or sell crypto or make a trade. The exchange holds the wallet’s private keys. While convenient, exchanges also have a checkered past, marred with breaches, hacks, and locked accounts that prevent access. One saying in crypto has proven correct over time: “Not your keys, not your coins.” Let’s learn how to choose a crypto wallet that protects your private keys and lets you navigate the crypto sphere your way.
The way you expect to use your crypto and the amount of crypto you hold often drive the decision regarding which type of wallet to use. Hot wallets make it easier to interact with decentralized applications (dApps), but they store the private keys on an internet-connected device. Cold wallets store the private keys offline.
The type of device you’ll use with your wallet also plays a role. For example, some mobile wallets support iOS but not Android. Others, including hardware wallets, might support Windows and macOS but not Linux. Some crypto wallets are only available as a browser extension, which makes them compatible with any desktop operating system but creates some security concerns.
You’ll also want to consider public and private key control. Exchange wallets are custodial, meaning the crypto exchange holds the keys. Non-custodial wallets give the user control of the keys. By some estimates, as much as $1.38 billion in crypto was stolen in the first half of 2024, with compromised seed phrases and private keys being the most common attack vectors. This number is likely underreported due to crypto’s unregulated nature.
Let’s examine some of today’s best crypto wallet choices in more detail, starting with hot vs. cold wallets.
First, let’s discuss hot wallets versus cold wallets. The distinction between the two centers on whether the private keys are generated and stored on a device that’s connected to the internet. Anyone who gains access to the private keys can control your crypto assets on the blockchain. Connected devices can create a risk.

Many hot wallets support select hardware wallets, such as Ledger devices. This combination of wallets lets you connect physical devices to dApps while securing the private keys controlling your crypto on a separate device.
Navigating the crypto world is easier on a desktop device than on a mobile device. However, you’ll find many of the leading crypto wallets support both platforms, allowing you to do your crypto thing at home or on the go. For example, MetaMask, Trust Wallet, and Coinbase Wallet all provide mobile apps as well as browser extensions.
Desktop wallets come in the form of standalone apps or (more often) browser extensions. Generally, hardware wallets offer better support for desktops as well.
Mobile wallets for Android or iOS are mobile apps, many offering access to a selection of dApps built into the interface. However, connecting to apps running in a separate browser app can be challenging in some cases.
Most desktop and mobile wallets support simple features like sending, receiving, and swapping one crypto for another. However, a desktop wallet is often easier for more complex interactions, such as navigating DeFi applications.
Custodial versus non-custodial refers to whether a third party controls the private keys or you control them. For example, if you have a trading account with a crypto exchange like Coinbase, the exchange holds the keys to a custodial wallet on your behalf.
Custodial Wallets
With a custodial wallet, you access the wallet’s funds by logging into the exchange and using the crypto you hold there to trade, but you don’t have access to the private keys. By contrast, if you download a crypto wallet and withdraw your crypto from the exchange to your new wallet, you control the private keys to the new wallet.
Custodial wallets are vulnerable to breaches, such as someone gaining access to your exchange account. In some cases, exchanges may also freeze accounts, blocking access to your account or the ability to withdraw. On the other hand, custodial crypto wallets provided by exchanges offer the easiest solution if you’ll just be trading and don’t keep much money on the platform.
By contrast, non-custodial crypto wallets, like MetaMask, allow only you to control the wallet’s private keys. In most cases, this is achieved by using a 12 or 24-word seed phrase that generates the wallet’s private keys through cryptography.
However, this also makes you responsible for safeguarding your wallet’s seed phrase (and private keys). If you ever lose access to the seed phrase, you won’t be able to access your crypto. Additionally, if someone else gets your seed phrase or private key, they can access your crypto.
Let’s examine some key factors and questions that can help you choose a crypto wallet. These center on the way you expect to use your crypto as well as security and cost.
The type of wallet you choose might depend on which cryptocurrencies you want to use. For example, you can’t send Ether (ETH) to a Bitcoin wallet. Each blockchain is an island unto its own in that regard. If you want to use the Ethereum blockchain, you’ll need a wallet that supports the Ethereum chain. The same applies to Bitcoin, Solana, Sui, and countless other chains. However, many time-tested non-custodial wallets support more than one type of cryptocurrency.
Consider how you’ll use your crypto. Simple storage or sensing and receiving don’t require special features. However, if you plan to use your crypto for on-chain activities, such as decentralized finance (DeFi), you’ll want a wallet that is well-supported by the protocols you need to use. For example, Aave, one of the leading lending and borrowing platforms, supports several browser-extension wallets, as well as Torus, a wallet that uses social logins to secure your private keys.
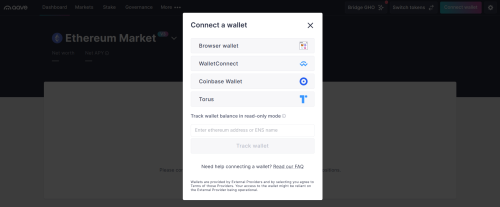
As discussed earlier, custodial wallets mean that a third party, like a crypto exchange, controls the private keys. New traders find this easier, which makes onboarding easier for the exchange. However, in addition to security concerns, this structure also limits how you can use your crypto. Although the earlier Aave screenshot shows Coinbase Wallet as an option, it does not refer to a custodial wallet on the Coinbase exchange. The exchange limits what you can do with funds stored in a custodial wallet. If you expect to venture off the exchange, a non-custodial wallet opens up a broader range of options.
Some wallets support enhanced security features, such as biometric authentication or even air-gapped technology, which removes the need to connect your wallet to any device when authorizing transactions. Some wallets also provide warnings before connecting to known scams or insecure applications. Many also provide warnings before buying a scam token.
Although free wallet apps can be full-featured, some use cases may make an investment in a premium wallet worthwhile. In most situations, this refers to buying a hardware wallet that stores your private keys offline. Depending on which wallet you buy and the features you need, expect to invest $50 to more than $500. Entry-level hardware wallets likely meet the needs of most beginners.
However, well-tested hot wallets can provide reasonable security for storing small amounts of crypto, and most are free to use. In a later section, we’ll discuss how to use a hot wallet in combination with a cold wallet to get the best of both worlds.
The crypto networks you need to use drive the decision when choosing a crypto wallet. Several popular wallets support multiple networks. However, for some tasks, you may also want to use a specialized wallet that supports one blockchain or a group of similar chains, such as EVM-compatible networks. EVM is an abbreviation for Ethereum Virtual Machine, a smart contract environment used by dozens of blockchains.
First, let’s compare some of the leading wallets to learn which chains they currently support. Be aware that these can change over time. For example, Phantom, a popular Solana wallet, recently added support for EVM chains. However, Coinbase Wallet stopped supporting four chains in 2023.
Notably, while some wallets may support storage and sending or receiving for specific cryptocurrencies, support for additional on-chain activities may be limited. Research the wallet you’re considering for compatibility with the protocols you expect to use. In some cases, support for chains must be “enabled” and won’t be immediately apparent.
As the name suggests, multi-chain wallets provide support for multiple blockchains. In the table from the previous section, four of the wallets supported all the blockchains we checked. Specialized wallets support one blockchain or a group of similar blockchains. For example, MetaMask and Rabby both support dozens of EVM-compatible blockchains. However, neither wallet supports BTC, XRP, Dogecoin, or Cardano.
While specialized wallets don’t offer broad blockchain support, they often excel at specific tasks. For instance, if you want to use your crypto in decentralized finance applications on an EVM chain, a specialized wallet like MetaMask or Rabby will make the experience much easier. Multi-chain wallets represent a tradeoff in usability, in many cases, providing support for more chains but adding complexity to web3 navigation.
Similarly, specialized wallets may offer additional features specific to the blockchain you’re using. For example, efficient use of Bitcoin can require occasional management of Unspent Transaction Outputs (UTXOs). Specialized Bitcoin wallets like Sparrow and Electrum support UTXO optimization. Multi-chain wallets are unlikely to support this feature, leading to higher transaction fees without explanation.
Privacy features can also distinguish specialty wallets from multi-chain wallets. For example, Sparrow (Bitcoin only) supports connections to Bitcoin nodes via The Onion Router (TOR), which enhances privacy by masking your true IP address.
When to Choose a Multi-Chain Wallet
Multi-chain wallets bring several advantages, most of which center around convenience and simplicity. Let’s examine situations in which you may want to choose a multi-chain wallet over a specialized crypto wallet.
Examples: Trust Wallet, Atomic Wallet, Exodus, Coinbase Wallet
When to Choose a Specialized Wallet
There’s a proper tool for every job, and that time-tested adage also applies to crypto wallets. Specialized wallets excel at specific tasks, such as interacting with smart-contract protocols, trading on decentralized exchanges (DEXs), or managing UTXOs for chains like Bitcoin. Let’s look at use cases in which a specialized wallet may be a better choice.
Examples: MetaMask, Rabby, Phantom, Solflare, Sparrow, Electrum
Over half of all total value locked (TVL) in crypto resides on the Ethereum blockchain. TVL measures assets used in smart contracts. Much of this value is locked in longer-term applications, such as staking. By contrast, other applications, such as lending or meme coin trades, benefit from a more nimble solution that lets users exit a position quickly.
Cold wallets are best for long-term holdings, whereas hot wallets are best for use cases that require more frequent access. Let’s compare hot and cold wallets to better understand which use cases and priorities suit each wallet type.
Next, let’s explore a few questions that can help you choose the right crypto wallet.
A cold wallet offers a more secure option if you intend to buy and hold for a longer period of time. However, you aren’t limited to a cold wallet. Leading hardware wallets like Ledger and Trezor can work with specialized wallets like MetaMask or Electrum. We’ll explain this strategy of using hot and cold wallets together in more detail later.
A hot wallet offers a more convenient solution if you expect to use your crypto often and the value is relatively low.
This consideration hinges on the value of your coins in large part. If you have more to protect, investing in a cold wallet that offers protection against online threats by storing your private keys offline may be wiser. Again, it is possible to pair cold storage with supported hot wallets.
However, hot wallets are much more convenient than cold wallets as standalone solutions. In most cases, a password or fingerprint is all that stands between you and your next trade or transaction. By contrast, using a cold wallet requires connecting it (or sending a QR code if using an air-gapped wallet). The spy-game allure may not last if you value convenience. If you place more value on security, a cold wallet is the clear choice.
Convenience aside, a cold wallet offers a much more secure storage option if you plan to hold a large amount of crypto. If you’re stepping out the back door momentarily, you probably don’t lock your house. If you’re going away for a week, you lock the doors and windows, set the alarm, and put the lights on timers. Risk management decisions hinge on the level of exposure.
Considering this, the amount of crypto at risk may not merit the costs and lost convenience of using a hardware wallet.
Decentralized applications, including DeFi and web3 gaming, are among the more popular blockchain uses. However, you’ll likely need a hot wallet to use these applications. Some crypto holders store smaller amounts of crypto in hot wallets for easy access to DEXs and defi platforms while using a cold wallet to store larger amounts. Pairing a hot wallet with a cold wallet lets you use larger amounts of crypto in trades on smart contracts while still protecting your private keys offline.
Almost all wallet apps and cold wallets give you control over your private keys. A handful use workarounds like social logins to abstract the complexity of crypto wallets. On the other hand, custodial wallets, such as those available through crypto exchanges, do not give the user control over the private keys. Instead, custodial wallets let you access your funds through a login to the platform.
Let’s review these types of wallets again because they differ regarding who controls the private keys.
Many users choose to withdraw their crypto from exchanges to a non-custodial wallet when they are done trading or after a purchase. The reasons behind this often center on maintaining control of their crypto funds. However, this step also allows you to use your crypto in other ways, such as spending on everyday transactions or using decentralized applications.
Most exchange wallets never encounter a problem, but several risks arise from using a custodial wallet.
Using a non-custodial wallet allows you to sidestep these risks, although the timing of withdrawals to a self-custody wallet becomes critical. However, you should use a non-custodial wallet only if you have a secure way to back up your seed phrase offline. This seed phrase allows you to restore your wallet if it becomes inaccessible due to hardware failure or other reasons.
Crypto exchanges and brokerages offer non-custodial wallets. Users do not get access to the seed phrase or private keys, and your crypto usage may be limited to activities on the platform or sending and receiving. However, this type of wallet is much easier to use. You don’t need to store the seed phrase securely because you don’t have access to it. Instead, you must practice good password safety and enable two-factor authentication to secure your funds. Be aware of the risks mentioned in the previous section, including frozen funds and exchange hacks.
If you expect you’ll only use crypto on the exchange itself and practice good account safety, a custodial wallet offers a much easier way to store your crypto, using a login similar to using online banking or payment services.
Crypto wallets offer various security features, such as two-factor authentication or offline key storage. However, there’s little crossover between these features and wallet types, with specific features common to a certain kind of crypto wallet. For example, many mobile wallets offer biometric authentication, but this feature isn’t common to hardware wallets.
Generally speaking, custodial exchange wallets rank lower in security features. This is mainly because the exchange holds the wallet’s private keys, and users have little transparency in how these keys are safeguarded. Additionally, accounts without two-factor authentication are only protected by a login.
Let’s examine some of these features in more detail to better understand their benefits and limitations. Crypto wallets and their corresponding security features usually fall into one of three categories: basic security, enhanced security, or highest security.
Wallets with basic security include exchange wallets. This type of wallet is designed to be user-friendly and allow easy access to funds. For example, you can access many exchange wallets with just a username and a password. Features like two-factor authentication may be optional and might include SMS-based authentication, which is a less safe option.
Examples of basic security wallets include exchange wallets like Coinbase and Binance or brokerage accounts like Robinhood and eToro. Notably, basic security wallets do not give users access to the wallet’s private keys. As such, funds can be frozen, or withdrawals can be suspended.
Wallets with enhanced security give users control over the wallet’s seed phrases and private keys. You’ll find some crossover here because both hot and cold self-custody wallets offer private key control. However, cold wallets fall into the next category (highest security) due to their offline cold storage.
Seed Phrases: Enhanced security wallets typically use a seed phrase that allows you to restore the wallet or, in some cases, use the wallet with multiple wallet apps.
Private Keys: Each wallet address has a unique private key used to authorize transactions. The wallet’s private keys are generated by a seed phrase but can be exported individually if you want to use just one of the wallet addresses elsewhere.
Examples of enhanced security wallets include specialized wallets like MetaMask (EVM chains) or Sparrow (Bitcoin only). Notably, many enhanced security wallet apps also support connections to hardware wallets that offer cold storage.
The highest-security options range from cold storage (storing the private keys offline) to hidden wallets and even wallets that require signatures from two or more external wallets. Let’s explore some of the more advanced features that may be available with the highest-security wallets, which are often hardware devices like Ledger or Trezor.
Don’t expect to find all of these features in a single wallet or app. You may need to prioritize according to your expected usage and risk level. Hardware wallets, such as time-tested brands like Ledger or Trezor, are among the highest-security crypto wallets. A wave of new players now also offers innovative crypto wallets. For example, Ellipal has become popular for its airgap wallets.
The highest-security options typically require an investment. Hardware wallet prices begin at about $50 and can cost hundreds of dollars for premium models. On the other hand, exchange wallets are free to use. However, there’s also a middle ground with free-to-use wallet apps, such as MetaMask or Electrum, which give you control over your private keys.
Electrum, MetaMask, Rabby, Sparrow, and several other well-supported wallet apps allow users to connect to select hardware wallets. This option allows users to protect larger balances with offline key storage while allowing them to interact with dApps or perform other tasks, such as managing UTXOs for Bitcoin or similar cryptocurrencies.
The hot wallet, such as MetaMask, connects to dApps, such as the Uniswap DEX, to swap cryptocurrencies or manage liquidity positions. However, with this structure, the private keys for specific wallet addresses are held on an external hardware wallet. The hot wallet app passes the transaction to the hardware wallet for authentication. If the transaction looks correct, you authorize it using the hardware wallet. Without the hardware wallet, the hot wallet cannot process transactions for the protected wallet addresses.
Many experienced crypto users utilize both hot and cold wallets, sometimes using these two options together as described or sometimes keeping them completely separate. The idea is similar to how we interact with traditional currencies, carrying some pocket money while keeping larger amounts in the bank or securely hidden.
Learning how to choose a crypto wallet requires examining your needs and risk level. Exchange wallets offer the easiest solution but do not give you access to your private keys. As a result, the risk is that funds could be stolen or your account could be compromised. Hot wallets give you control over your private keys but may still be susceptible to vulnerabilities. Hardware wallets offer the best protection because they store the private keys offline. However, the added security comes at a cost. You’ll need to buy a hardware wallet if your needs demand the extra security of offline private key storage.
Exchange wallets offer the easiest onboarding experience. However, hot wallet apps, like Coinbase Wallet or Trust Wallet, also offer a user-friendly interface and give you control over your wallet’s private keys.
Consider moving to a cold wallet if your crypto asset balances are high or if you expect your cryptocurrency to significantly grow in value.
Yes, if you have a significant amount of cryptocurrency, using a hot wallet in combination with a cold wallet allows you to store your larger balances securely while still having access to smaller balances and the ability to connect to third-party dApps with reduced risk.
Cold storage is the most secure way to store crypto. With cold storage, the private keys that control your crypto assets on the blockchain are stored offline.
In addition to matching the wallet’s features to your needs, it’s crucial to choose a crypto wallet you trust. Newer wallet apps may have yet-undiscovered vulnerabilities. Hot wallets with open-source code, active development, and vibrant user communities or hardware wallets from well-established makers often make the safest choices.
Source: cryptonews.com
Your email address will not be published.
[…] January 2022, the number of cryptocurrencies existing in the market increased by 1 thousand. This implies that each new…
Your writing is like a breath of fresh air in the often stale world of online content. Your unique perspective…
I would like to share my story and express my great gratitude to Maria. My husband Alexander was literally taken…